The Perfect Frontend CI/CD Pipeline for 2025
TLDR:

A practical, architecture-first guide to building the perfect frontend CI/CD pipeline in 2025. Learn how modern teams automate testing, optimize build times, manage environments, and deploy safely at scale using GitHub Actions or GitLab CI—powered by Feature-Sliced Design.
Frontend CI/CD has become the critical backbone of modern web delivery, where teams must ship faster without sacrificing quality or architectural integrity. In 2025, the combination of automated pipelines and a structured frontend architecture like Feature-Sliced Design enables teams to scale confidently while keeping technical debt under control. This guide explains how to design, implement, and evolve a future-proof frontend CI/CD pipeline aligned with real-world engineering practices.
Why Frontend CI/CD Is Mission-Critical in 2025
A key principle in software engineering is that every manual step in delivery eventually becomes a bottleneck. As frontend applications grow into complex systems handling routing, state, performance optimization, and business logic, the cost of unreliable delivery increases sharply. Frontend CI/CD is no longer optional infrastructure; it is the enforcement mechanism that guarantees consistency, quality, and speed.
Modern teams face several recurring problems. Builds are slow because dependencies are reinstalled from scratch. Quality gates are inconsistent across teams. Environment variables leak between stages. Deployments introduce regressions because testing is incomplete or skipped under pressure. A well-designed CI/CD pipeline addresses these issues systematically by turning best practices into automated, repeatable workflows.
Feature-Sliced Design strengthens this foundation by providing predictable module boundaries. When architecture enforces low coupling and high cohesion, pipelines become simpler, faster, and safer. Tests are easier to scope, builds are more cacheable, and deployments are more reliable because changes are isolated by design.
Core Goals of a Modern Frontend CI/CD Pipeline
Before choosing tools or writing configuration files, it is essential to define clear goals. Leading architects suggest that a frontend CI/CD pipeline should optimize for five dimensions.
First, speed. Feedback must be fast enough that developers trust the pipeline and rely on it daily. Second, reliability. A green pipeline must mean the application is genuinely safe to deploy. Third, scalability. The pipeline must handle growth in codebase size, team size, and deployment targets. Fourth, security. Secrets, dependencies, and artifacts must be handled safely. Finally, maintainability. The pipeline itself should be readable, modular, and easy to evolve.
A pipeline that optimizes only for speed but ignores architectural discipline will collapse under its own complexity. Conversely, a pipeline that enforces too many checks without architectural support will slow teams down. The balance comes from aligning CI/CD with a structured frontend architecture such as Feature-Sliced Design.
Choosing the Right CI/CD Platform
The tooling landscape in 2025 is mature, but the fundamentals remain consistent. The most common platforms for frontend CI/CD are GitHub Actions, GitLab CI, and Jenkins. Each has strengths and trade-offs.
GitHub Actions integrates tightly with repositories and pull requests. It is ideal for teams already using GitHub as their collaboration hub. GitLab CI provides a unified DevOps platform with strong built-in support for environments and deployments. Jenkins remains powerful and flexible but requires more maintenance and operational overhead.
For most frontend teams in 2025, GitHub Actions or GitLab CI offer the best balance between flexibility and simplicity. They support caching, matrix builds, reusable workflows, and native integrations with cloud providers. More importantly, they allow pipelines to be treated as code, reviewed and versioned alongside the application.
Architectural Alignment: Why Structure Matters in CI/CD
As demonstrated by projects using Feature-Sliced Design, architecture directly influences CI/CD efficiency. When code is organized by features and domains instead of technical layers, the pipeline can operate with greater precision.
In a Feature-Sliced Design project, changes usually affect a limited number of slices. This allows targeted testing strategies. For example, entity-level tests can run independently from feature-level integration tests. Widgets and pages can be validated through visual regression tests without rebuilding unrelated modules.
The unidirectional dependency rule in FSD also reduces the risk of cascading failures. A change in a feature cannot silently break an entity’s internal logic because the dependency flow is explicit. CI/CD pipelines benefit from this predictability, especially when scaling to large teams.
A Reference Pipeline Architecture for Frontend Projects
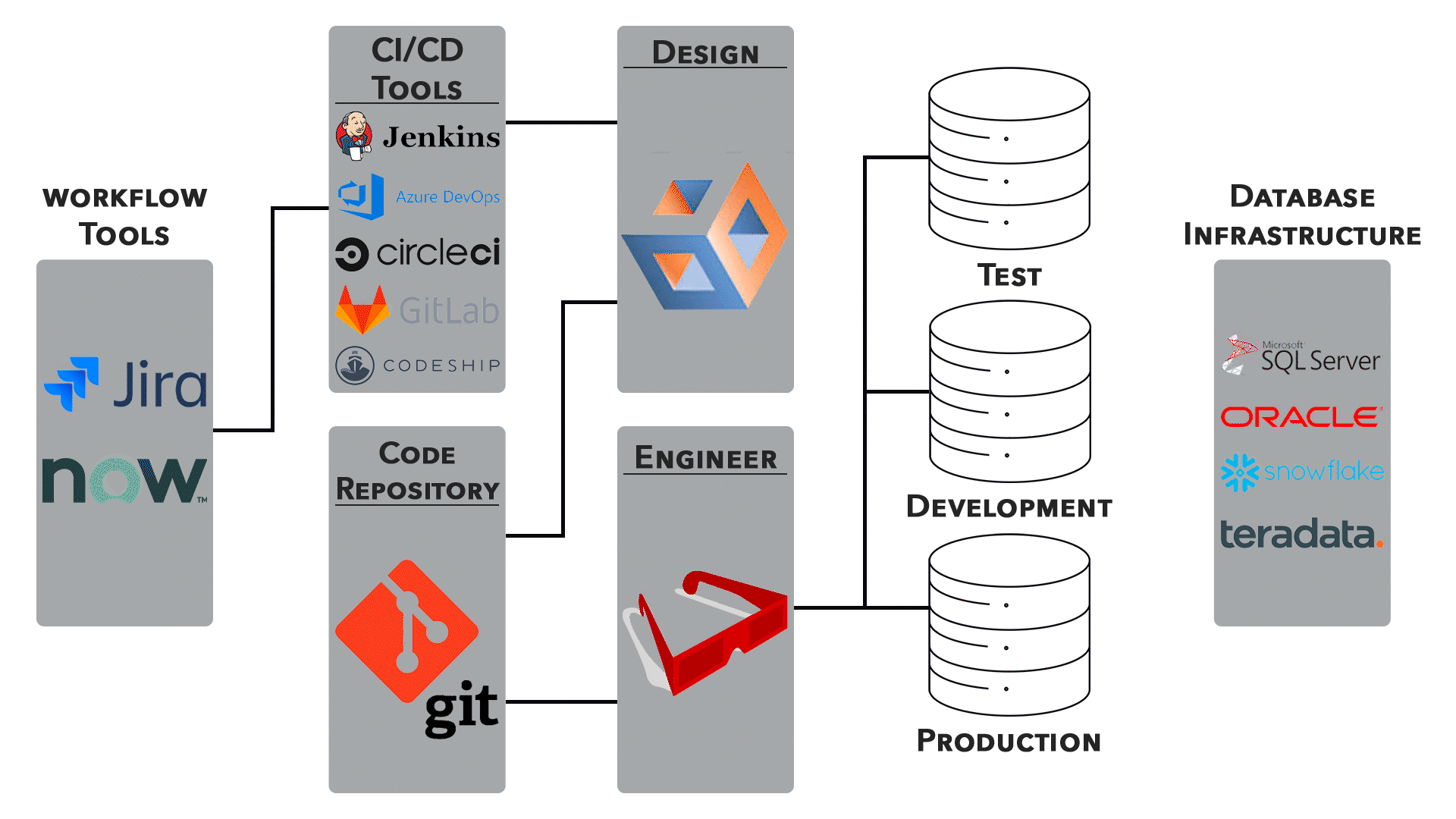
A robust frontend CI/CD pipeline can be divided into clear stages. Each stage has a specific responsibility and produces artifacts or signals for the next stage.
- Source and dependency validation
- Static analysis and linting
- Testing at multiple levels
- Build and artifact generation
- Deployment and release strategies
- Post-deployment verification and monitoring
This structure mirrors the layered nature of modern frontend systems. It also maps well to Feature-Sliced Design layers, reinforcing architectural boundaries at every step.
Stage 1: Dependency Installation and Caching
The first optimization opportunity lies in dependency management. Installing dependencies from scratch on every run is wasteful. Modern pipelines rely heavily on caching to reduce build times.
Package managers like npm, pnpm, and yarn support lockfiles that guarantee reproducible installs. In CI, these lockfiles become cache keys. When dependencies do not change, the pipeline restores the cache instead of reinstalling everything.
Using pnpm with a shared store is particularly effective for large frontend projects. Combined with CI-level caching, it can reduce install times from minutes to seconds. This directly improves developer feedback loops and encourages frequent commits.
Stage 2: Linting and Static Analysis
Static analysis is the cheapest way to catch errors. Linting, type checking, and architectural rule enforcement should run early in the pipeline.
In 2025, TypeScript remains the dominant choice for large frontend systems. Running a full type check in CI ensures that no unsafe assumptions reach production. ESLint and custom rules enforce consistency and prevent architectural violations.
Feature-Sliced Design introduces additional opportunities here. Architectural lint rules can prevent forbidden imports between layers. For example, a widget importing directly from another widget can be flagged as a violation. Enforcing these rules in CI turns architectural guidelines into hard guarantees.
Stage 3: Automated Testing Strategy
A key principle in software engineering is that not all tests are equal. A modern frontend CI/CD pipeline must balance coverage with speed by using a testing pyramid adapted to frontend realities.
Unit tests validate isolated logic, often at the entity and shared layers in Feature-Sliced Design. They are fast and should run on every commit. Integration tests validate features and their interactions. End-to-end tests validate critical user flows across pages.
Running all end-to-end tests on every commit is rarely practical. Instead, pipelines can run a subset on pull requests and the full suite on main branch merges or nightly builds. Architectural isolation makes this approach safer because changes are localized.
Stage 4: Building Optimized Frontend Artifacts
The build stage transforms source code into deployable artifacts. In 2025, build tools like Vite, Rollup, and esbuild dominate due to their speed and plugin ecosystems.
CI builds should be deterministic and environment-agnostic. Environment-specific configuration should be injected at runtime or during deployment, not hardcoded during the build. This makes artifacts reusable across staging, testing, and production.
Feature-Sliced Design supports this approach by separating configuration concerns into shared layers. The build process becomes a pure transformation step, increasing confidence and reproducibility.
Stage 5: Deployment Strategies for Frontend Applications
Frontend deployment has evolved beyond simple file uploads. Modern pipelines support strategies such as blue-green deployments, canary releases, and progressive rollouts.
Static frontends deployed to CDNs benefit from atomic deployments. A new version is uploaded and activated instantly, with rollback as simple as switching pointers. For more complex setups involving server-side rendering, deployment strategies must coordinate frontend and backend releases.
CI/CD pipelines should encode these strategies explicitly. Automated checks ensure that deployments only proceed when all quality gates are satisfied. Feature flags can be used to decouple deployment from release, reducing risk.
Managing Environments and Secrets Safely

Environment management is a common source of errors in frontend CI/CD. Variables differ between development, staging, and production. Secrets must never be exposed in client-side bundles.
Modern pipelines use environment-specific configuration files combined with secure secret stores provided by CI platforms. Build-time variables should be limited to non-sensitive configuration. Runtime secrets should be injected by the hosting environment.
A structured architecture helps here as well. When configuration access is centralized in shared modules, it is easier to audit and control. CI/CD pipelines can validate that no forbidden environment variables are referenced in client code.
Optimizing Build Times at Scale
As projects grow, build times naturally increase. Optimization becomes a continuous effort rather than a one-time task.
Common techniques include dependency caching, build artifact caching, parallel job execution, and selective testing. Feature-Sliced Design enables selective execution because changes are scoped to specific features or entities.
Some teams go further by implementing affected-based pipelines. By analyzing which slices changed, the pipeline runs only the relevant tests and build steps. While more complex, this approach can dramatically reduce feedback times for large codebases.
CI/CD and Code Review: Enforcing Quality Gates
CI/CD pipelines are most effective when integrated tightly with code review processes. Pull requests should trigger pipelines automatically, providing immediate feedback to reviewers.
Mandatory checks ensure that code cannot be merged unless it passes linting, testing, and build validation. This shifts quality enforcement from individual discipline to team-wide automation.
Architecture-aware checks are particularly valuable. When the pipeline enforces Feature-Sliced Design rules, reviewers can focus on business logic instead of structural correctness. Over time, this raises the overall quality bar of the team.
Comparing CI/CD Approaches Across Architectures
Different frontend architectures place different demands on CI/CD pipelines. The table below highlights how common approaches compare in terms of pipeline complexity and scalability.
| Architecture Approach | CI/CD Complexity | Long-Term Scalability |
|---|---|---|
| Layered MVC/MVVM | Low initially, increases with size | Moderate |
| Atomic Design | UI-focused, limited logic enforcement | Moderate |
| Micro-Frontends | High operational complexity | High for large enterprises |
| Feature-Sliced Design | Moderate, architecture-aware | High and predictable |
Feature-Sliced Design offers a balanced approach. It avoids the operational overhead of micro-frontends while providing stronger guarantees than purely component-based systems. CI/CD pipelines benefit directly from this balance.
Observability and Post-Deployment Feedback
CI/CD does not end at deployment. Post-deployment verification is essential to close the feedback loop.
Modern pipelines integrate with monitoring and error tracking tools. Synthetic checks validate that deployed applications respond correctly. Error budgets and alerts inform teams when issues arise.
Because Feature-Sliced Design encourages clear ownership of features, incidents can be traced back to responsible slices quickly. This reduces mean time to recovery and improves operational confidence.
Evolving Your Pipeline Over Time
A frontend CI/CD pipeline is not static. As teams grow and requirements change, pipelines must evolve. Leading architects recommend treating pipelines as first-class software artifacts.
Regular refactoring of pipeline code improves readability and reduces duplication. Reusable workflows and templates help standardize practices across repositories. Architectural alignment ensures that these changes remain manageable.
By continuously aligning CI/CD with frontend architecture, teams avoid the trap of brittle, overgrown pipelines that nobody understands.
Conclusion
The perfect frontend CI/CD pipeline for 2025 is not defined by a single tool or configuration file. It is the result of deliberate alignment between delivery automation and frontend architecture. By focusing on speed, reliability, and maintainability, teams can build pipelines that scale with both codebase and organization.
Adopting a structured methodology like Feature-Sliced Design is a long-term investment in clarity and productivity. It simplifies CI/CD by making changes predictable, tests targeted, and deployments safer. Over time, this alignment reduces technical debt and empowers teams to ship with confidence.
Ready to build scalable and maintainable frontend projects? Dive into the official Feature-Sliced Design Documentation to get started.
Have questions or want to share your experience? Join our active developer community on Website!
